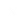OUR CORE SERVICE OFFERINGS
Enterprise Data Architecture
An enterprise data architecture framework (EDAF) is a structured approach to managing and organizing data within an organization. It encompasses the entire data lifecycle, from collection and storage to processing and analysis.
Federal Enterprise Architecture Framework (FEAF)
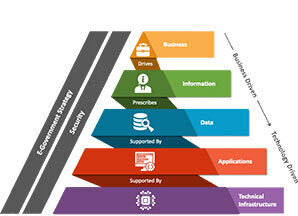
FEAF designed to provide a common approach for the practice of Enterprise Architecture (EA) across the U.S. Federal Government. Components: • Business Architecture: Defines what is done, by whom, how, when, and why. • Data Architecture: Focuses on the information used by the agency to conduct business. • Application Architecture: Encompasses the software applications that process data according to defined business rules. • Technology Architecture: Covers the hardware and communications technology supporting the other three layers.
Department of Defense Architecture Framework (DODAF) v2.0
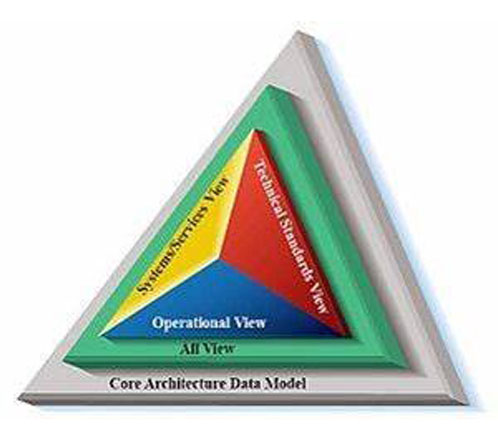
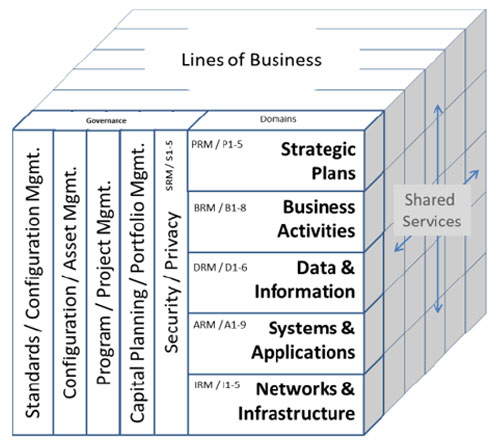
Department of Defense Architecture Framework (DODAF) A comprehensive framework used by the U.S. Department of Defense (DoD) to develop and manage enterprise architectures. It provides a structured approach for representing and visualizing the architecture of DoD systems, ensuring that all stakeholders have a clear and consistent understanding of the system’s structure and behavior.
Zachman Enterprise Framework
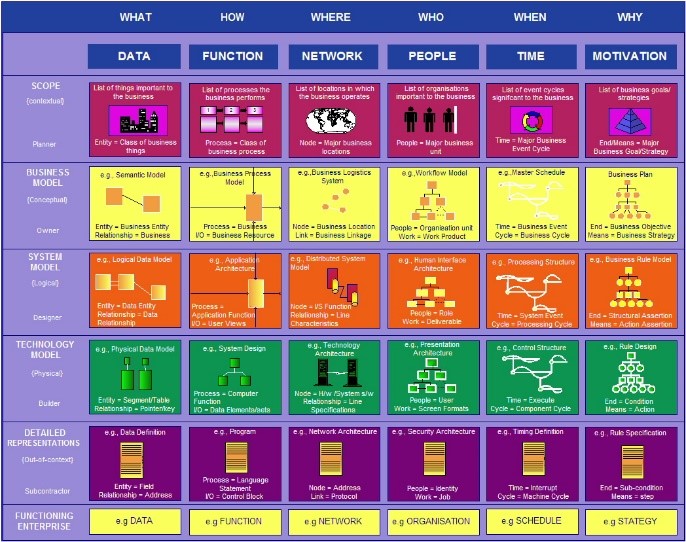
1. Two-Dimensional Classification Schema: Interrogatives: What, How, When, Who, Where, and Why. 2. Matrix Structure: The framework is typically depicted as a 6x6 matrix, with the interrogatives as columns and the reification transformations as rows. 3. Enterprise Ontology: It serves as an ontology, providing a theory of the existence of a structured set of essential components of an enterprise. 4. Not a Methodology: The Zachman Framework is not a methodology for creating implementations but rather a schema for organizing architectural artifacts.
Operational Technology & Security Framework
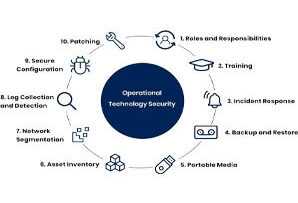
Operational Technology (OT) cybersecurity focuses on protecting the hardware and software that manage and control physical devices and processes in industrial environments. Key aspects of OT cybersecurity include: 1. Ensuring Continuity and Safety: OT security practices aim to maintain the continuous operation of critical infrastructure and industrial processes, ensuring they run safely and efficiently1. 2. Protecting Legacy Systems: Many OT environments use older systems that were not designed with cybersecurity in mind. 3. Managing Unique Protocols: OT environments often use specialized communication protocols that differ from traditional IT networks.
The Open Group Architecture Framework
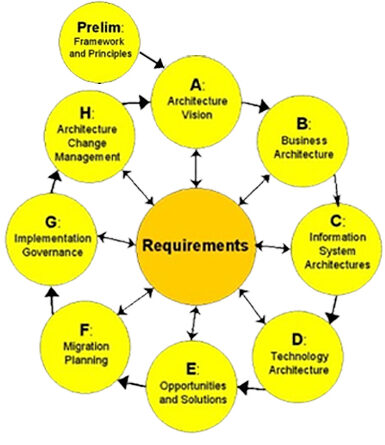
The TOGAF (The Open Group Architecture Framework) a globally recognized credential for enterprise architecture. provides an approach for designing, planning, implementing, and governing an enterprise information technology architecture. A high-level approach to design. It is typically modeled at four levels: Business, Application, Data, and Technology. It relies heavily on modularization, standardization, and already existing, proven technologies and products.
NIST Risk Management Framework (RMF)

The Risk Management Framework (RMF) provides a process that integrates security, privacy, and cyber supply chain risk management activities into the system development life cycle. The risk-based approach to control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, Executive Orders, policies, standards, or regulations. Managing organizational risk is paramount to effective information security and privacy programs; the RMF approach can be applied to new and legacy systems, any type of system or technology (e.g., IoT, control systems), and within any type of organization regardless of size or sector.
AWS 6 Pillars of a “Well-Architected” Framework
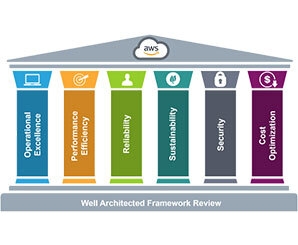
The AWS Well-Architected Framework documents a set of foundational questions that help you to understand if a specific architecture aligns well with cloud best practices. The framework provides a consistent approach to evaluating systems against the qualities you expect from modern cloud-based systems, and the remediation that would be required to achieve those qualities. As AWS continues to evolve, and we continue to learn more from working with our customers, we will continue to refine the definition of well-architected.